In the ever-evolving threat landscape, it is not a matter of ‘if’ but rather ‘when’ a cybersecurity breach occurs. Acting swiftly and effectively can enhance an organization’s cyber resilience and restore it to its secure state. However, this isn’t easy with conventional security platforms. SOCs have too many tools. They have too many alerts. They have too few people to comb through millions of threat alerts to locate that one real threat. They need security automation.
Unable to cope with the sheer scale of security alerts, dozens of tools to deal with, and false positives, security teams who already face staff shortages feel overwhelmed. The result—many alerts sneak by, leaving the organization vulnerable to security breaches.
The fact is, it is humanly not possible for analysts to respond to every single alert. So the question then is how do security teams protect the organization despite being severely understaffed?
Security automation prioritizes security alerts
There are only 24 hours in a day, so making the best use of that time behooves your security posture. Security automation using an intelligent automation platform connects and orchestrates disparate security tools and feeds to provide your security analysts more research time. Automating the incident management process using intelligent automation and AI provides enterprises information on which alerts need immediate attention. By eliminating time-consuming administration processes and centralizing communication, teams can more effectively neutralize attacks, reduce human error and reduce the meantime to recovery (MTTR).
Security organizations have too much to do
ESG recently surveyed security professionals to reveal: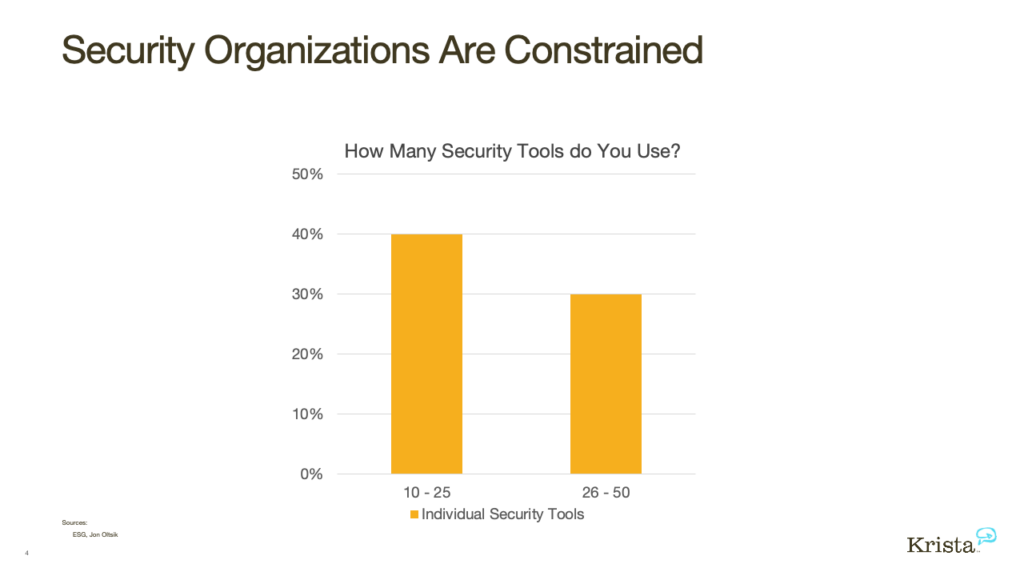
- 40% of security organizations use 10 to 25 different tools, while 30% use around 26 to 50.
- 27% of cybersecurity professionals say they receive too many alerts.
- 35% say that one of the biggest challenges is managing an assortment of point tools.
- 51% of these organizations have a shortage of staff.
As the above data shows, there is a shortage of trained staff to respond to millions of alerts. To add to it, SOC teams are primarily involved in doing repeatable, mundane tasks instead of focusing on higher priority tasks, which is to respond and research security threats. Further, security teams are grappling with an overload of point tools adding to the confusion. Together this can be a recipe for disaster leading to devastating consequences for the organization.
The technology should adapt to your security analysts
The problem is not with automation per se but the fact that we have not been able to make automation adapt to our workforce. For decades, we have asked our people to learn and adapt to technology instead of having technology adapt to us. Machines and technology get faster and faster–humans do not. It’s time we start depending more on technology and powerful artificial intelligence.
Intelligent automation integrates people and systems
Intelligent automation, or “hyperautomation,” as Gartner refers to it, uses technology to automate tasks that once required humans. It’s not replacing humans but uses advanced technologies, including artificial intelligence (AI) and machine learning (ML), to increasingly automate processes and augment humans. Instead, it’s about transforming business outcomes with digital technologies so your people can perform more critical work.
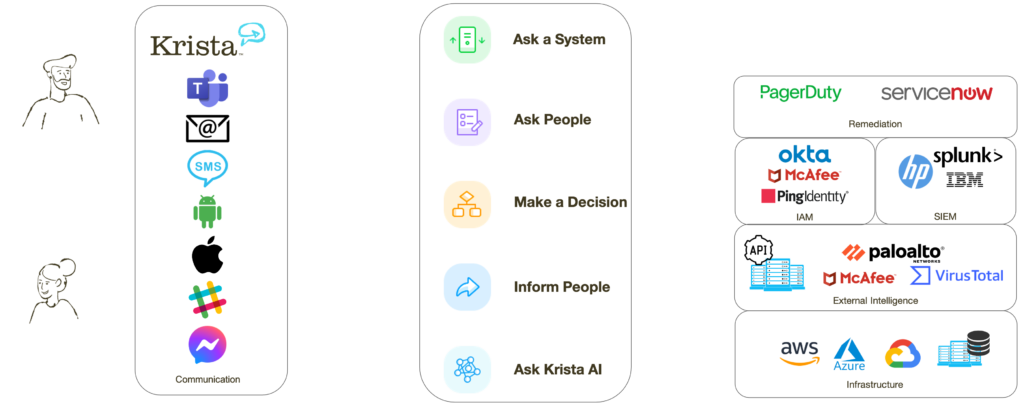
Krista connects your people and existing systems
Krista is an intelligent platform that connects the processes, people, and technologies you already have in your organization. It integrates with your existing systems to afford you greater visibility while minimizing dwell time and expediting time to repair. Krista breaks down silos between people and systems by leveraging conversation across the organization. If you know how to have a conversation with other human beings, you know how to use Krista. It’s as simple as that!
Typically, handling a system alert and fixing it requires significant coordination between teams and associated knowledge handovers. Even after successfully deploying the fix, the investigation of the issue remains in different incident tickets. If you need to perform a lesson learned exercise, one has to scan through the chronology of all these tickets to understand how the separate security teams handled this alert. While this may sound simple, the actual overhead and communicating across teams and across time zones can prove challenging.
Krista can do all of that simply by having a conversation with people and systems. When a conversation itself is the automation, it’s easy to maintain it as you don’t need specific knowledge of APIs or programming language to deal with it. Through orchestration and automation, Krista can intuitively perform a series of actions in a matter of seconds to simplify threat detection. It helps escalate alerts that are dangerous to the system and need remedial action.
Krista automates compliance and documentation
 Compliance, access control, visibility rules, and enterprise-grade security are some rules you need to be aware of in any cybersecurity SOC operation. For example, Krista has built-in enterprise role-based access control at the data level that allows you to see only those pieces of information you’re allowed to see based on your role. Role-based data security is essential since not all information is privy to all users in your organization.
Compliance, access control, visibility rules, and enterprise-grade security are some rules you need to be aware of in any cybersecurity SOC operation. For example, Krista has built-in enterprise role-based access control at the data level that allows you to see only those pieces of information you’re allowed to see based on your role. Role-based data security is essential since not all information is privy to all users in your organization.
By centralizing incident response processes using conversations, Krista logs each step and decision involved in researching alerts. So, if in the future you need information or to document precisely what happened with a specific incident, you don’t have to log in to multiple systems to figure out what happened. Instead, Krista can provide you data on the incident and build a report for you, saving you time and administrative headaches.
How Krista orchestrates your SOC
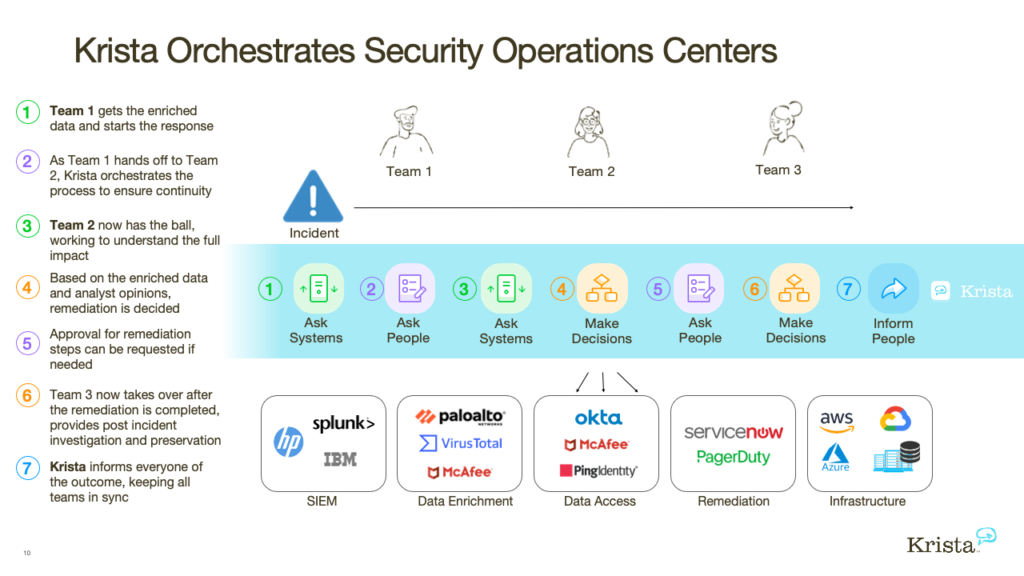
To give an example, let us see how an analyst might use Krista. When an alert appears, teams start checking multiple systems trying to figure out the data they have about it. Once they have deciphered the incident, they open a ticket making sure information routes to the right people. If multiple teams work in different time zones or shifts, the primary analyst must accurately provide data and information to the next team.
Here’s a walkthrough of how this works
- Krista connects with your disparate tools and systems to provide analysts with a single user interface for all security tools and feeds.
- Once an alert arrives, analysts can view threat intelligence data in a central system that simplifies research and automates documentation.
- If the primary team did not resolve the issue, it can hand off the conversation to a second team. Krista orchestrates the process to ensure continuity, ensuring the following teams have all relevant information and history–all within the same conversational workflow.
- If work on a specific alert continues, the second team then sends the conversation to a third team. Again, Krista provides all of the alert information within the same conversation.
- Krista informs everyone of the outcomes, keeping all teams in sync and updates connected systems.
Typically, this would have been a lengthy process. But with automation, it becomes a simple sequential operation. Automating incident management significantly reduces resolution times while simultaneously reduces the potential for errors. As a result, the procedure helps minimize time analyzing alerts, informs users, and updates connected systems to assist remediation.
Intelligent automation is sustainable automation
Krista is an intelligent platform that effectively integrates people, processes, and technology to provide the best solution for your organization. With firms possibly encountering millions of alerts a day, you need AI-led intelligent automation to help you create a more efficient and combative security program.